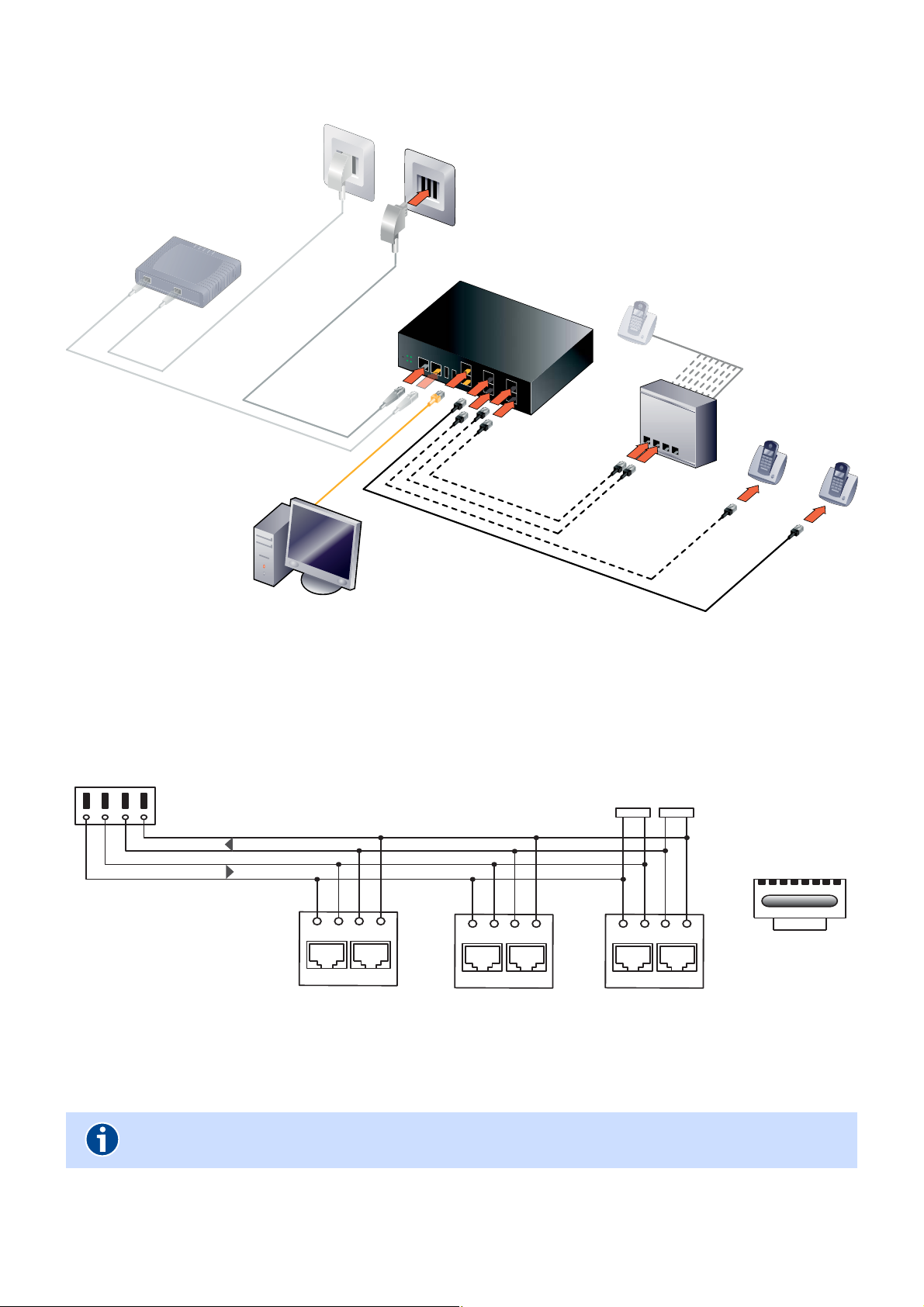
Gatewa
52
e) De
t
f
wh
of li
rec
All
in the
conta
is a
a fur
may
ment,
veyi
I
t
f
Addi
sepa
ei
8. T
You m
under
will
cens
Ho
ular
holde
copy
t
Mor
ly if the c
t
wo
your
Termi
par
ri
rec
9. Ac
You ar
Pr
quenc
quir
t
do not a
wo
10. Au
Eac
cens
t
with th
An “
subs
zati
par
licens
pre
wo
rea
You ma
or a
roy
may
legi
or i
11. Pa
A “contr
Pr
cal
A contri
by the c
infr
its
cons
t
cons
Eac
cens
sal
t
In the followin
commi
permi
“grant”
mitment n
If you
respondin
and unde
other readi
Source to
patent licens
the requ
cipients
patent li
use of th
ents in
If, pursuant to or i
vey, o
license to s
propaga
license
and w
A patent li
erage, p
more of
conve
is in the bu
third
which th
work from y
covered
ily for
ered wor
granted
Nothing i
cense
under a
12. No
If condit
that contr
ditions of
taneousl
then as
terms that o
whom
and t
13. Use wi
Notwit
or combin
Affero
sulting w
the cov
License, s
combin
14. Re
The Fr
GNU General
in spirit
conce
Each ver
that a cer
version
ther of t
ware Found
General Pu
Softwar
If the Prog
General
of a ver
Later l
no additi
of your
15. Discla
THERE IS NO WARRANTY
TED
ING THE COPY
PRO
PRESSED OR IMP
WARRANTIES OF MERCHA
PURPOSE. THE ENTIRE RISK AS TO THE QUA
THE P
TIVE
OR CO