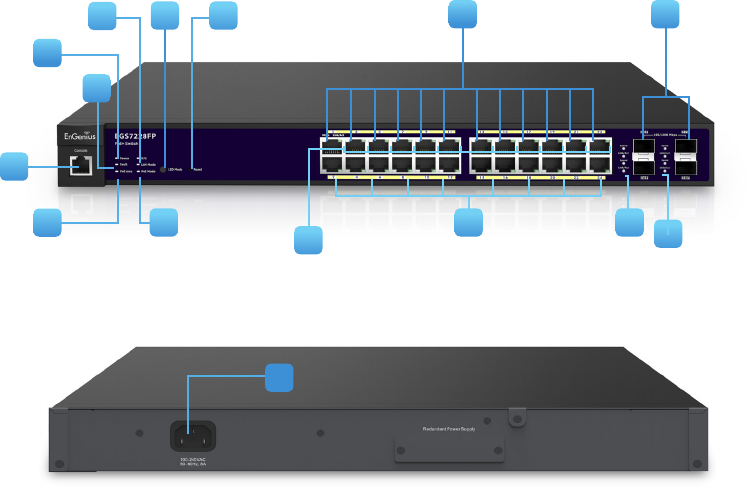
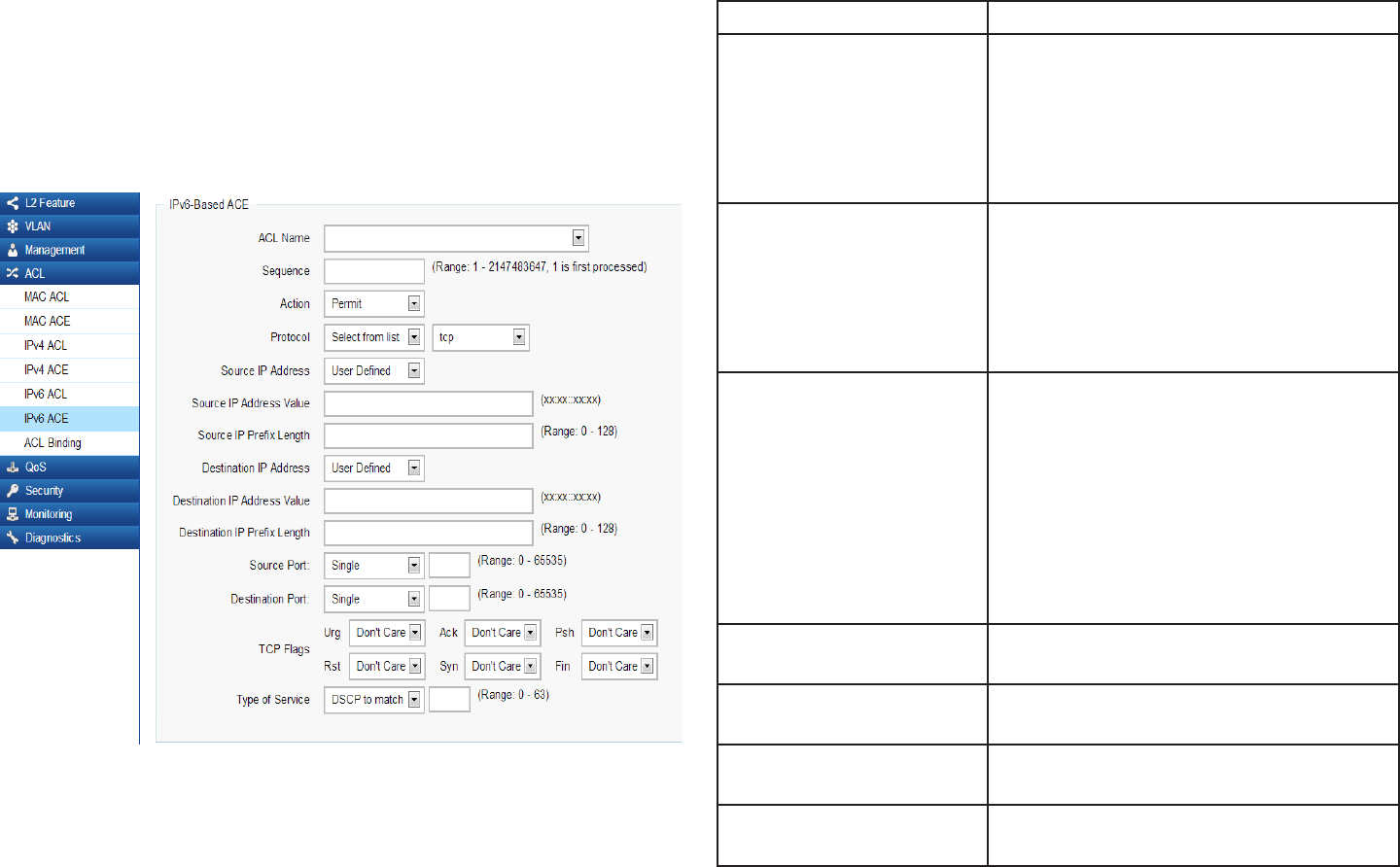
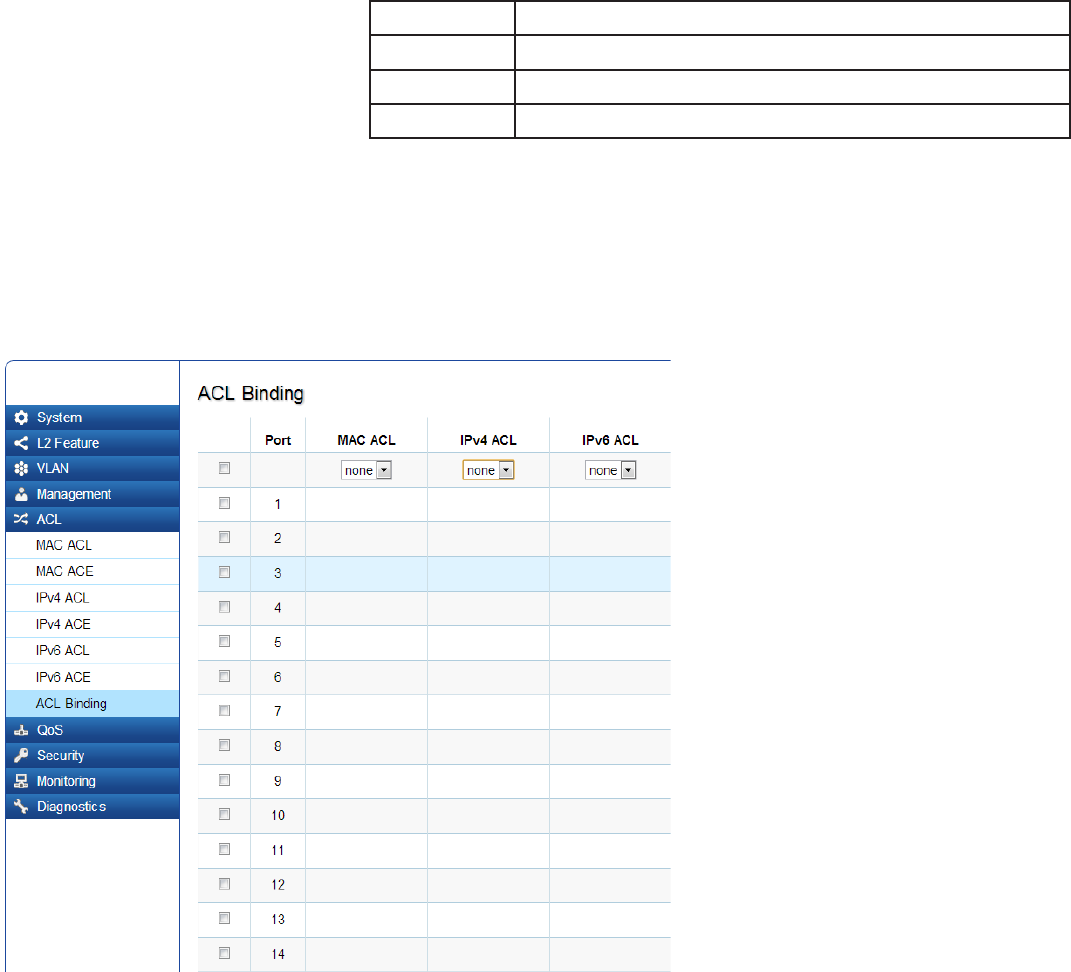
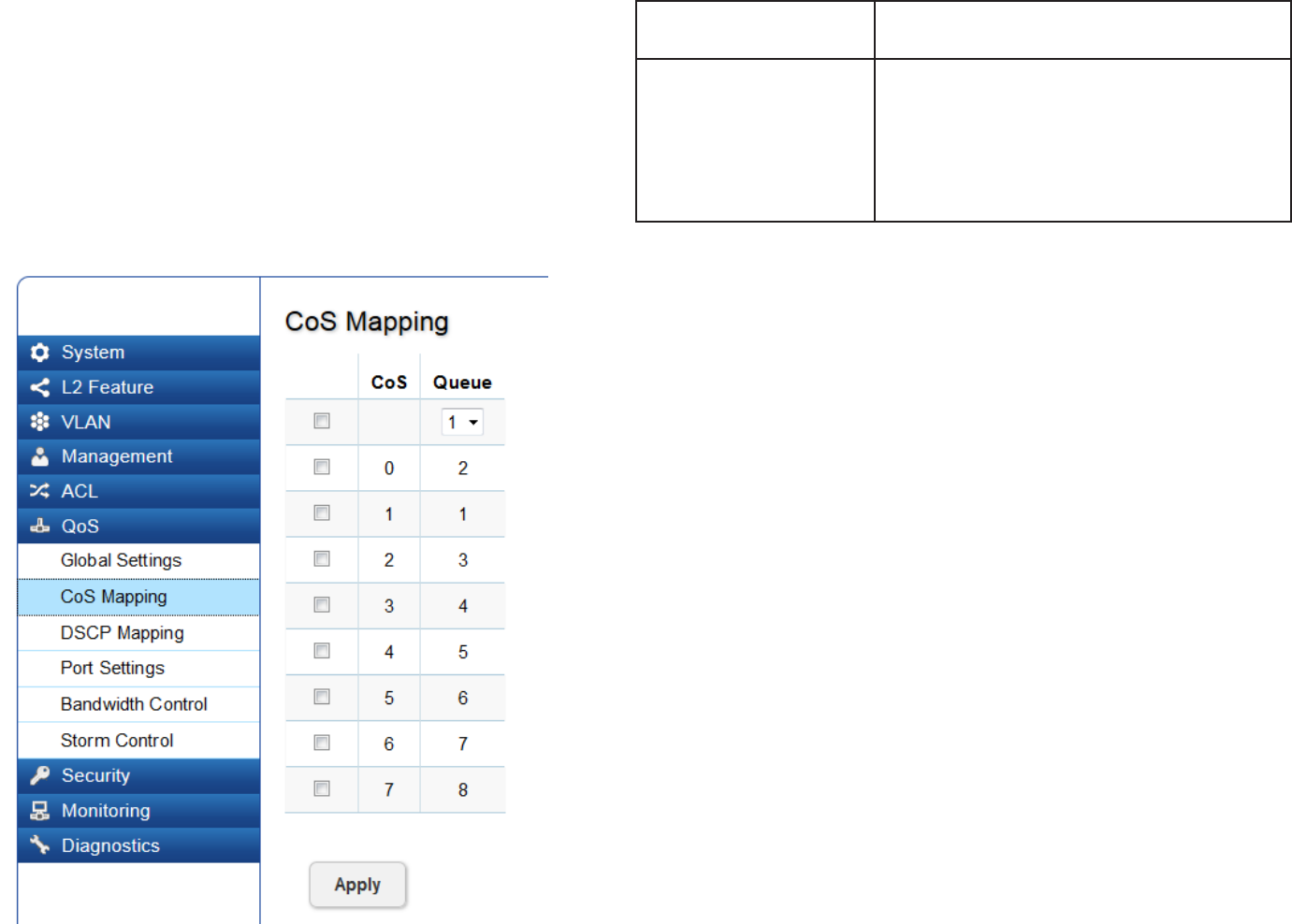
88
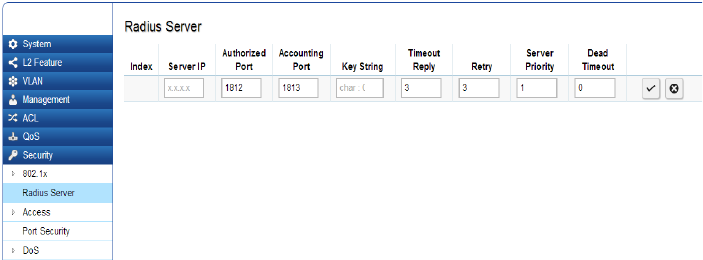
SNMP
Simple Network Management Protocol (SNMP) is an
ApplicationLayerprotocoldesignedspecicallyfor
managing and monitoring network devices. Simple
Network Management Protocol (SNMP) is a popular
protocol for network management. It is used for
collectinginformationfromandconguringnetwork
devices such as; servers, printers, hubs, Switches, and
routers on an Internet Protocol (IP) network. SNMP is
used to exchange management information between
a network management system (NMS) and a network
device. A manager station can manage and monitor the
Switch through their network via SNMPv1, v2c and v3.
An SNMP managed network consists of two components;
agents and a manager.
An agent translates the local management information
from the managed Switch into a form that is
compatible with SNMP. SNMP allows a manager
and agents to communicate with each other for
the purpose of accessing Management Information
Bases (MIBs). SNMP uses an extensible design,
wheretheavailableinformationisdenedbyMIBs.
MIBs describe the structure of the management
data of a device subsystem; they use a hierarchical
namespacecontainingObjectIdentiers(OID).EachOID
identiesavariablethatcanbereadorsetviaSNMP.
The manager is the console through which network ad-
ministrators perform network management functions.
Several versions of SNMP are supported. They are v1,
v2c,andv3.SNMPv1,whichisdenedinRFC1157“A
Simple Network Management Protocol (SNMP)”, is a stan-
dardthatdeneshowcommunicationoccursbetween
SNMP-capabledevicesandspeciestheSNMPmessage
types. Version 1 is the simplest and most basic of ver-
sions. There may be times where it’s required to support
olderhardware.SNMPv2c,whichisdenedinRFC1901
“Introduction to Community-Based SNMPv2,” RFC 1905,
“Protocol Operations for Version 2 of the Simple Network
Management Protocol (SNMPv2)”, and RFC 1906 “Trans-
port Mappings for Version 2 of the Simple Network Man-
agement Protocol (SNMPv2)”. SNMPv2c updates protocol
operations by introducing a GetBulk request and authen-
tication based on community names. Version 2c adds
several enhancements to the protocol, such as support
for “Informs”. Because of this, v2c has become the most
widelyusedversion.Unfortunately,amajorweakness
of v1 and v2c is security. To combat this, SNMP v3 adds
a security features that overcome the weaknesses in
v1 and v2c. . If possible, it is recommended that you use
v3- especially if you plan to transmit sensitive informa-
tion across unsecured links. However, the extra security
featuremakescongurationalittlemorecomplex.