On an infrastructure network, each access point (AP) is set to use a fixed channel, and
stations automatically detect the channel used by the AP that provides the best signal
quality. The
Channel control is therefore disabled when the Network Mode control is set
to
Infrastructure.
An ad-hoc network operates on a fixed channel. To join a given ad-hoc network, you
must select the correct channel from the
Channel control’s drop-down list. The settings
offered in the list depend on the regulations of the country in which the adapter was
purchased.
APs with overlapping coverage areas, or different ad-hoc networks operating in the same
area, should use channel settings that are at least four, and preferably five channels apart
(for example, 1, 6, and 11) to avoid interference and obtain the best possible performance.
Power Saving Mode
The Power Saving Mode control is a drop-down list that offers two settings:
Continuous Access Mode and Maximum Power Save.
In Continuous Access mode, your adapter’s receiver is always on.
Maximum Power Save mode is a “doze” mode in which the adapter turns its receiver off
but “wakes up” at fixed intervals to see if any communications are waiting for it. Before
entering this mode, it tells the AP (or, on an ad-hoc network, the current coordinating
station) that it is going to do so. The AP (or coordinating station) will “buffer”
(temporarily store) communications destined for your machine. The adapter stays
“awake” only long enough to check for and receive waiting communications..
4X Mode
The 4X Mode control is a drop-down list that offers two settings: Off and On.
The default setting is
On. When Mode 4x is On, it can therefore provide a higher data
rate (more than 22 Mbps), increased throughput, around two times greater range, than
other 802.11b-compliant adapters. Mode 4x can be used on wireless links to products in
the same family as your adapter.
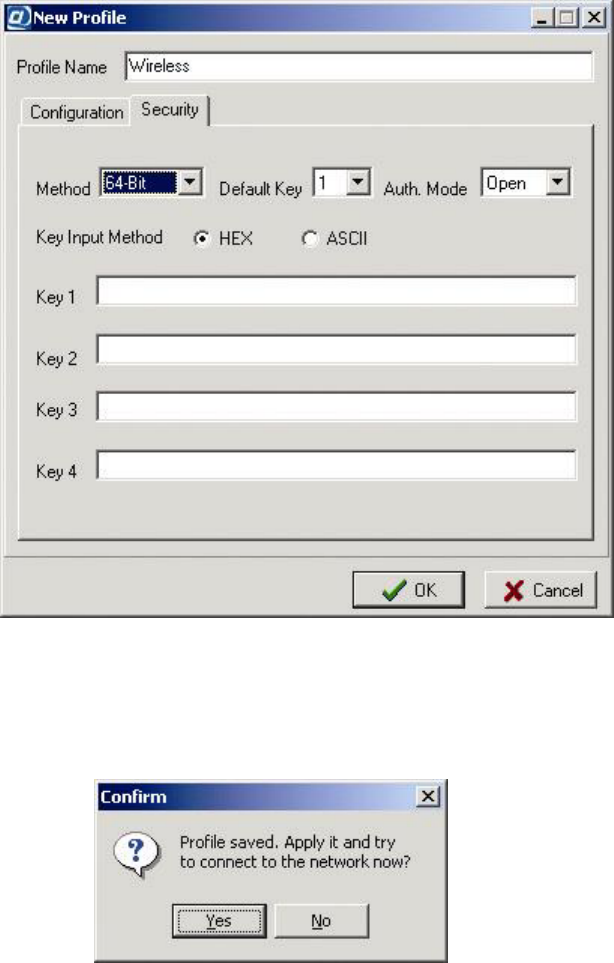
Security
The Security control is a drop-down list at Security panel’s Method for selecting a WEP
setting. Four settings are offered:
Disable, 64-Bit, 128- Bit, and 256-Bit.
The default setting is
Disable. Selecting any other setting enables the WEP key input
controls WEP itself is not enabled in the profile until you complete WEP key input.
If you select
64-Bit, 128- Bit, and 256-Bit, four WEP keys can be used. These keys
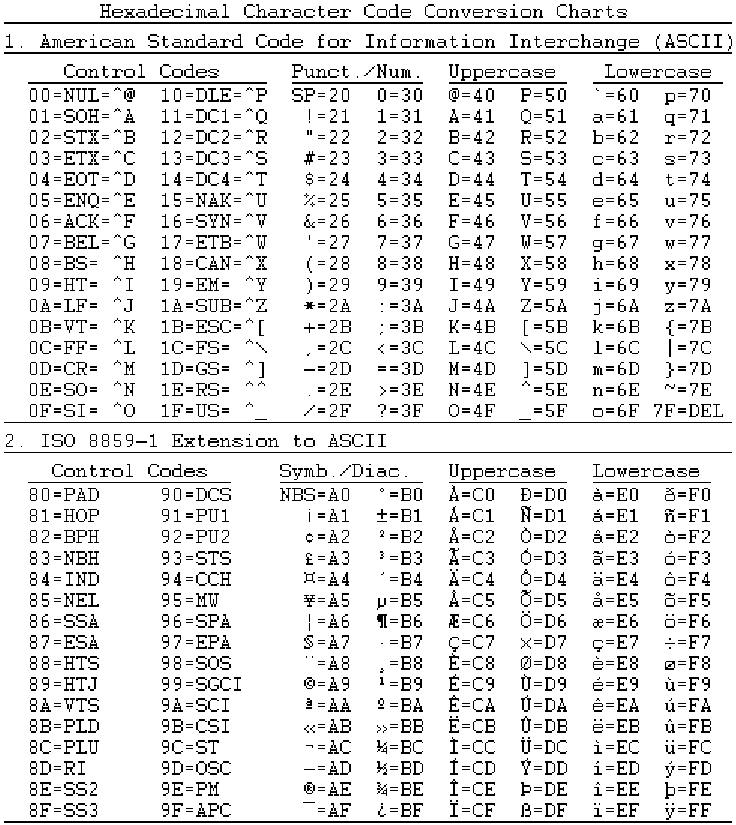
accept “hex” (hexadecimal, that is, base 16) notation or “ASCII” characters. In hex, the
numbers 0 through 9 and the letters A through F are all considered digits (the letters stand
for the values we normally refer to as ten through fifteen). When typing into one of these
keys you must type “0x” first, or your input is considered incomplete. The current key
must be selected here, or you will not be able to connect.
29