Table of Contents
CHAPTER 1. ACRONIS POWERUTILITIES .......................................................5
1.1 ABOUT ACRONIS POWERUTILITIES.................................................5
1.2 ABOUT THE ACRONIS POWERUTILITIES USER’S GUIDE .................6
1.3 SOFTWARE USAGE CONDITIONS ..................................................... 7
1.4 TECHNICAL SUPPORT ......................................................................7
CHAPTER 2. INSTALLING AND STARTING TO WORK WITH ACRONIS
POWERUTILITIES ................................................................................................8
2.1 ACRONIS POWERUTILITIES SYSTEM PACKAGE............................... 8
2.2 HARDWARE AND SOFTWARE REQUIREMENTS ................................ 8
2.3 INSTALLING ACRONIS POWERUTILITIES COMPONENTS .................8
2.4 RECOVERING ACRONIS POWERUTILITIES COMPONENTS................ 8
2.5 REMOVING ACRONIS POWERUTILITIES COMPONENTS ...................9
2.6 ACRONIS POWERUTILITIES SUITE INTERFACE................................9
2.7 RUNNING A SUITE COMPONENT......................................................9
CHAPTER 3. CLEANING USER ACTIVITY TRACES FROM A COMPUTER.....10
3.1 SOFTWARE LOGICAL ORGANIZATION: SECTIONS .........................10
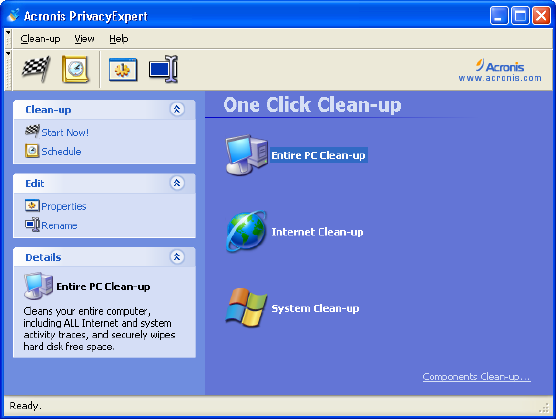
3.1.1 COMPLEX PC CLEAN-UP...........................................................................11
3.1.2 CLEANING SEPARATE SYSTEM COMPONENTS...........................................11
3.2 EXECUTING PC CLEAN-UP MANUALLY ........................................ 12
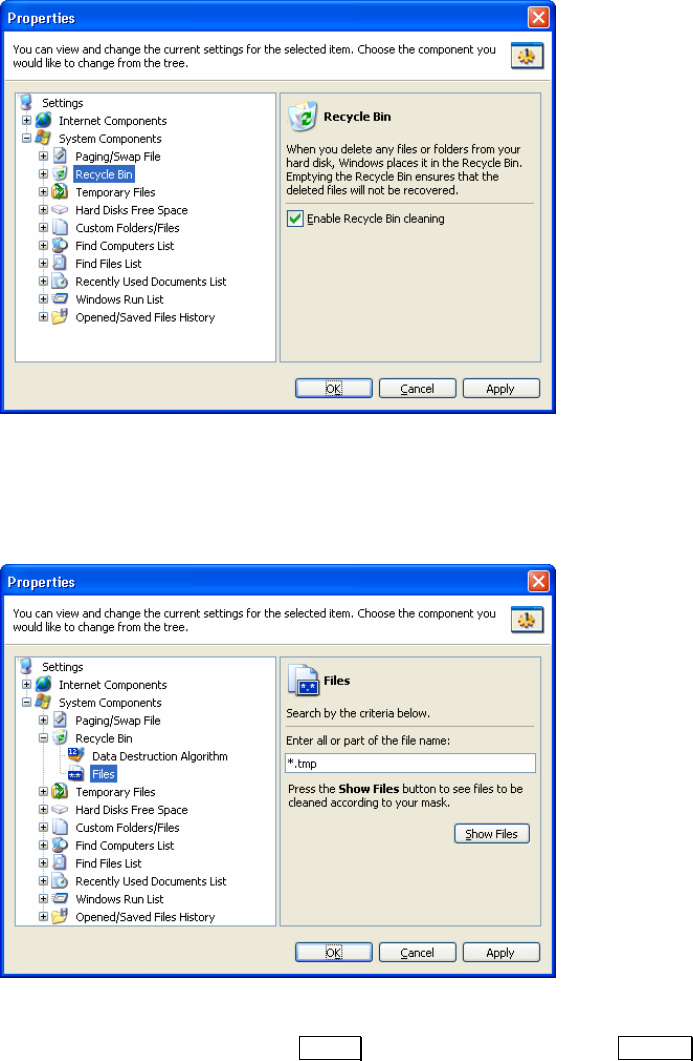
3.3 CLEAN-UP SETTINGS .....................................................................12
3.3.1 CLEAN-UP SETTINGS.................................................................................12
3.3.2 CLEAN-UP SETTINGS EDITOR....................................................................12
3.3.3 SETTING PC COMPONENT CLEAN-UP WITH THE EDITOR...........................12
3.4 SEPARATE COMPONENTS CLEAN-UP SETTINGS ............................ 14
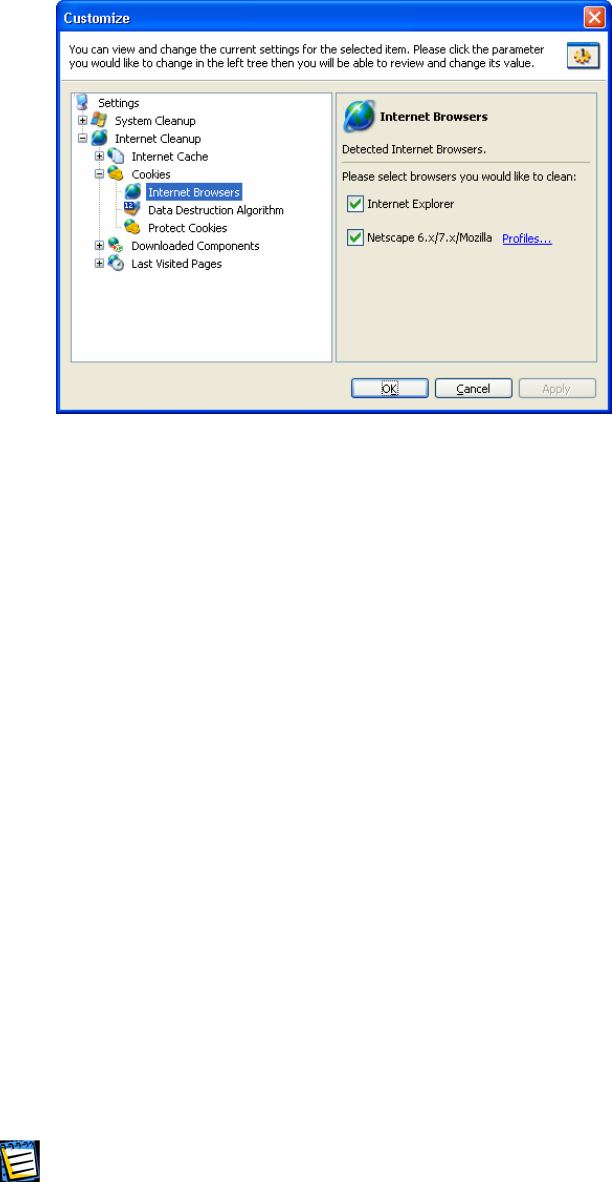
3.4.1 CLEAN-UP SETTINGS OF COMPONENTS RELATED TO WORKING ON THE INTERNET
.................................................................................................................14
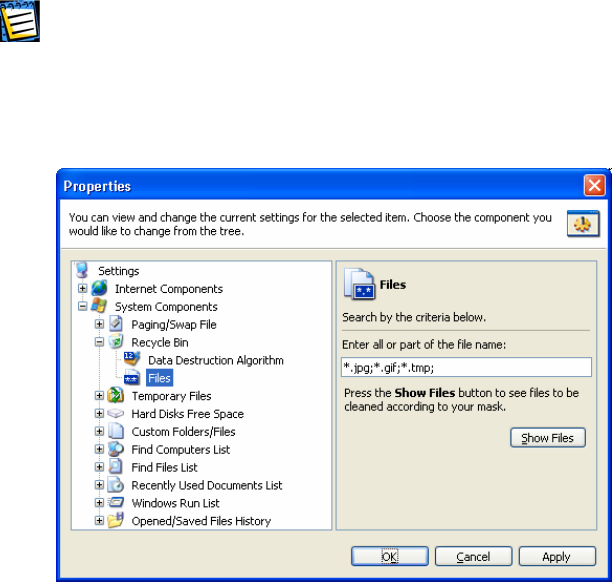
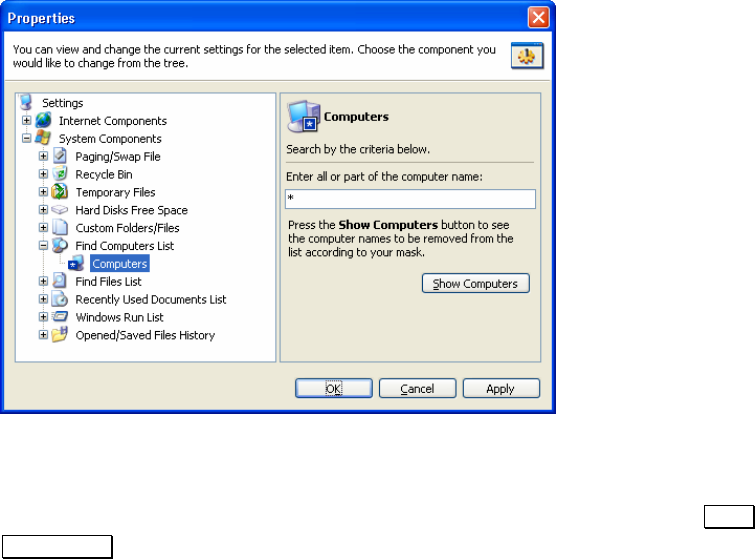
3.4.2 SYSTEM COMPONENT CLEAN-UP SETTINGS..............................................16
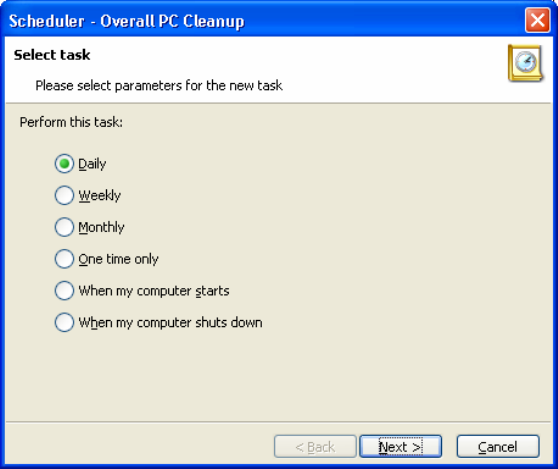
3.5 EXECUTING SCHEDULED PC CLEAN-UP........................................20
3.5.1 INVOKING THE SCHEDULER.........................................................................21
3.5.2 SCHEDULER SETTINGS..............................................................................21
3.6 RENAMING CLEAN-UP VARIANTS .................................................22
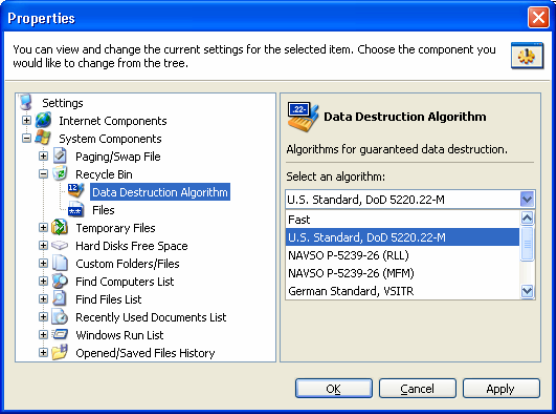
3.7 DATA CLEAN-UP ALGORITHMS..................................................... 22
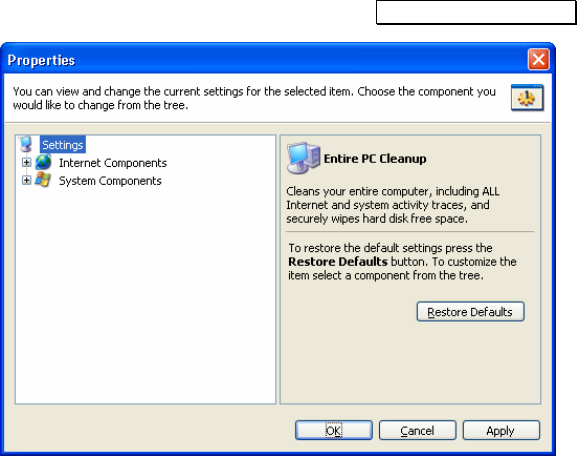
3.8 COMPLEX PC CLEAN-UP ...............................................................23
3.8.1 ENTIRE PC CLEAN-UP...............................................................................23
3.8.2 SYSTEM CLEAN-UP...................................................................................24
3.8.3 INTERNET CLEAN-UP ................................................................................24
3.9 A FAST CLEANUP OF SEPARATE SYSTEM COMPONENTS .............. 25
CHAPTER 4. MIGRATING DATA TO A NEW HARD DISK ..............................26
4.1 PREPARING FOR MIGRATION......................................................... 26
4.2 HARD DISK PARTITIONS AND FILE SYSTEMS................................26
4.3 INSTALLING A HARD DISK ON YOUR COMPUTER .........................27
4.4 BIOS SET-UP .................................................................................27
4.5 STARTING WORK WITH ACRONIS MIGRATEEASY ........................28
4.6 MIGRATION SCENARIOS ................................................................ 29
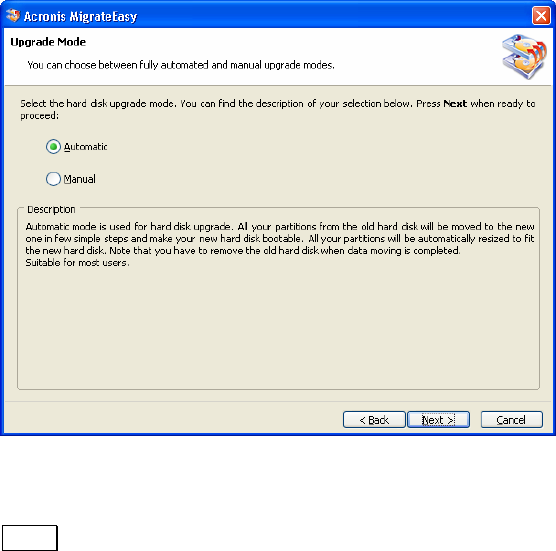
4.6.1 AUTO UPGRADE........................................................................................29
4.6.2 MANUAL UPGRADE ..................................................................................29
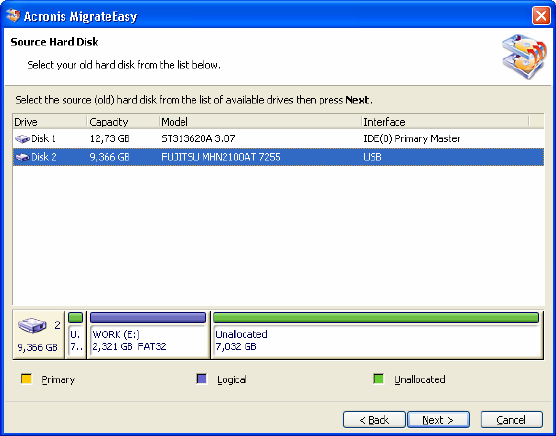
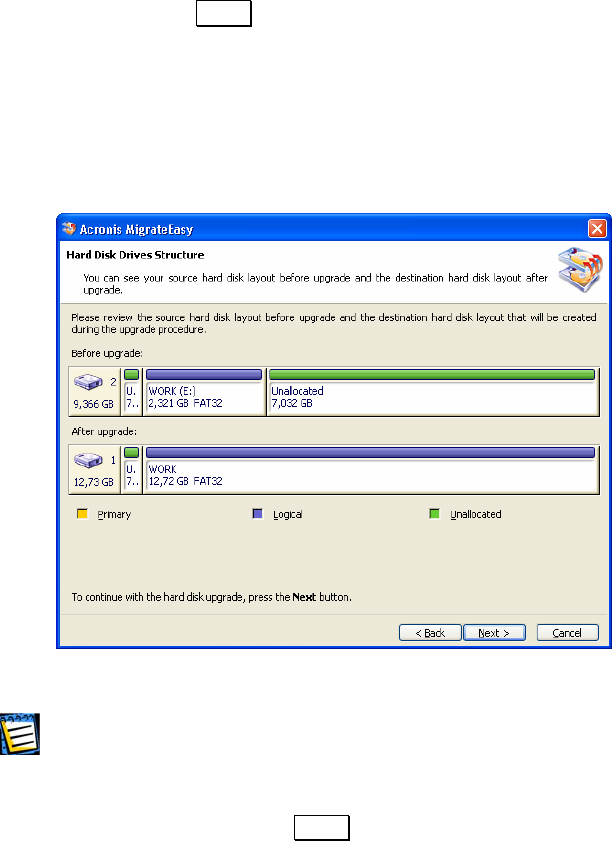
4.7 AUTO UPGRADE ............................................................................30
4.8 SAFETY.......................................................................................... 34
Acronis PowerUtilities
3