2 Copyright © Acronis International GmbH, 2002-2016
Table of contents
1 Administrator's Guide ......................................................................................................4
1.1 About this document ................................................................................................................. 4
1.2 What's new in version 5............................................................................................................. 4
1.3 About the backup service .......................................................................................................... 4
1.3.1 Accounts and groups ....................................................................................................................................... 4
1.3.2 Components .................................................................................................................................................... 5
1.3.3 Supported web browsers ............................................................................................................................... 7
1.4 Step-by-step instructions ........................................................................................................... 7
1.4.1 Activating the backup service subscription ................................................................................................... 7
1.4.2 Creating a group .............................................................................................................................................. 7
1.4.3 Creating an account ........................................................................................................................................ 8
1.4.4 Accessing the web consoles ........................................................................................................................... 9
1.4.5 Creating a report about the service usage .................................................................................................... 9
1.5 Advanced scenarios .................................................................................................................10
1.5.1 Deploying agents on client machines .......................................................................................................... 10
2 User's Guide .................................................................................................................. 12
2.1 About the backup service ........................................................................................................12
2.2 What's new in version 5...........................................................................................................12
2.3 Software requirements ............................................................................................................14
2.3.1 Supported web browsers ............................................................................................................................. 14
2.3.2 Supported operating systems and environments ...................................................................................... 14
2.3.3 Supported Microsoft SQL Server versions ................................................................................................... 15
2.3.4 Supported Microsoft Exchange Server versions ......................................................................................... 15
2.4 Activating the account .............................................................................................................16
2.5 Accessing the backup service ..................................................................................................16
2.6 Installing the software .............................................................................................................16
2.6.1 Preparation .................................................................................................................................................... 16
2.6.2 Proxy server settings ..................................................................................................................................... 18
2.6.3 Linux packages ............................................................................................................................................... 19
2.6.4 Installing agents ............................................................................................................................................. 21
2.6.5 Updating agents ............................................................................................................................................ 22
2.6.6 Uninstalling agents ........................................................................................................................................ 23
2.7 Backup console views ..............................................................................................................23
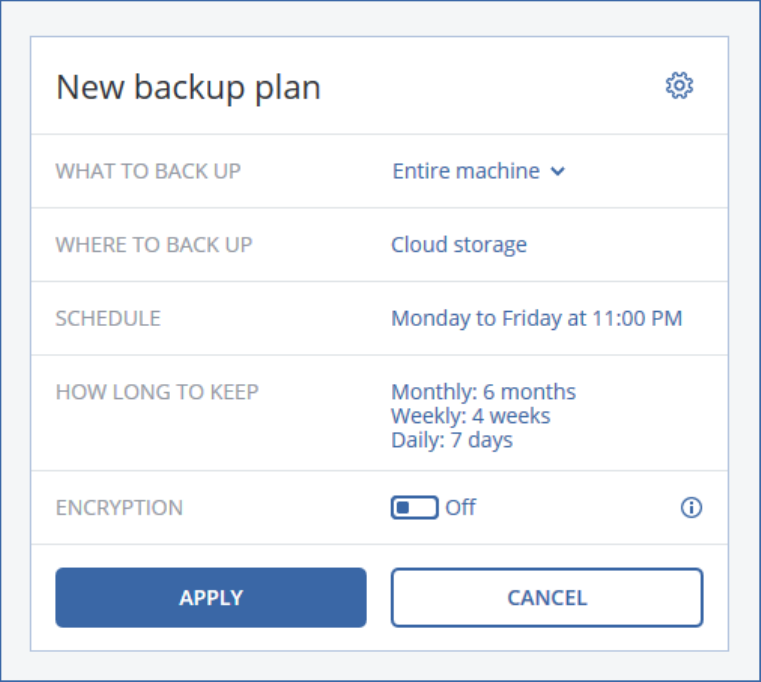
2.8 Backup .....................................................................................................................................24
2.8.1 Backup plan cheat sheet ............................................................................................................................... 26
2.8.2 Selecting data to back up .............................................................................................................................. 26
2.8.3 Selecting a destination .................................................................................................................................. 31
2.8.4 Schedule ......................................................................................................................................................... 32
2.8.5 Retention rules .............................................................................................................................................. 33
2.8.6 Replication ..................................................................................................................................................... 33
2.8.7 Encryption ...................................................................................................................................................... 34
2.8.8 Starting a backup manually .......................................................................................................................... 36
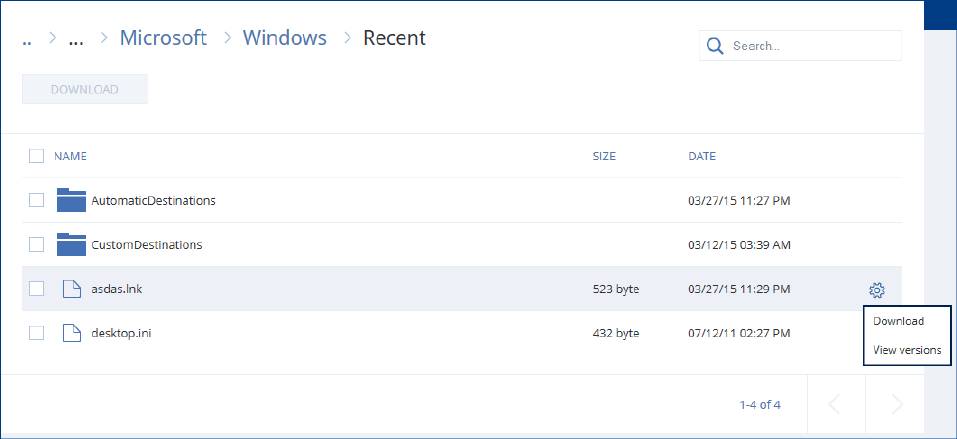
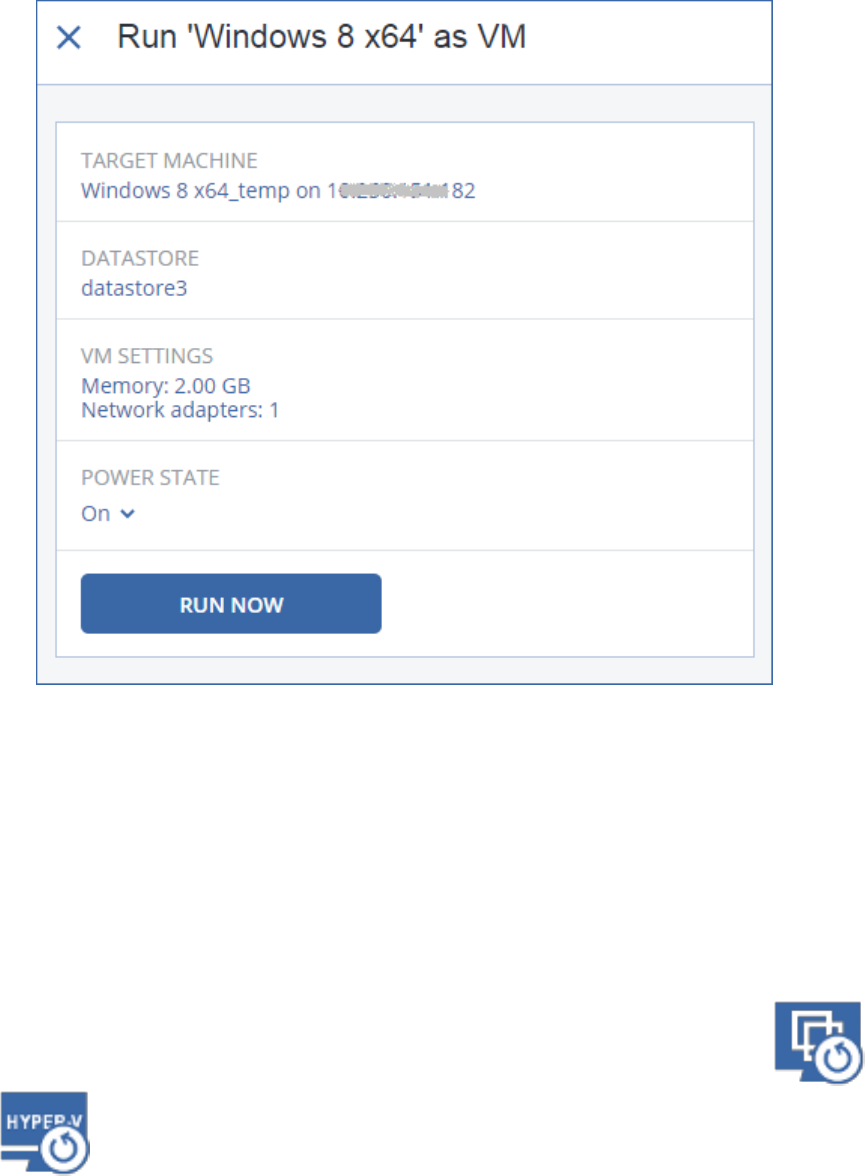
2.9 Recovery ..................................................................................................................................36
2.9.1 Recovery cheat sheet .................................................................................................................................... 36
2.9.2 Creating bootable media .............................................................................................................................. 36
2.9.3 Recovering a machine ................................................................................................................................... 37