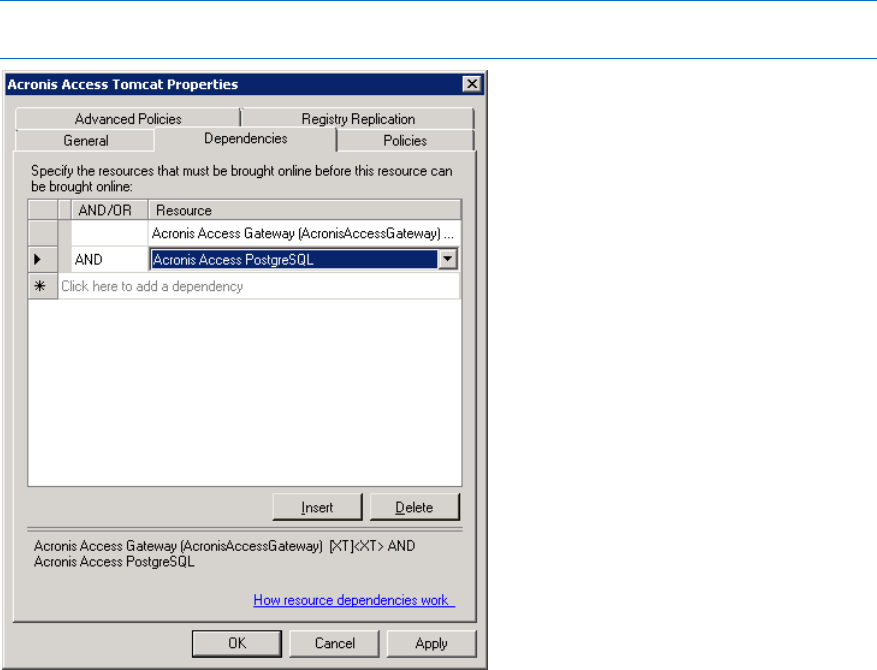
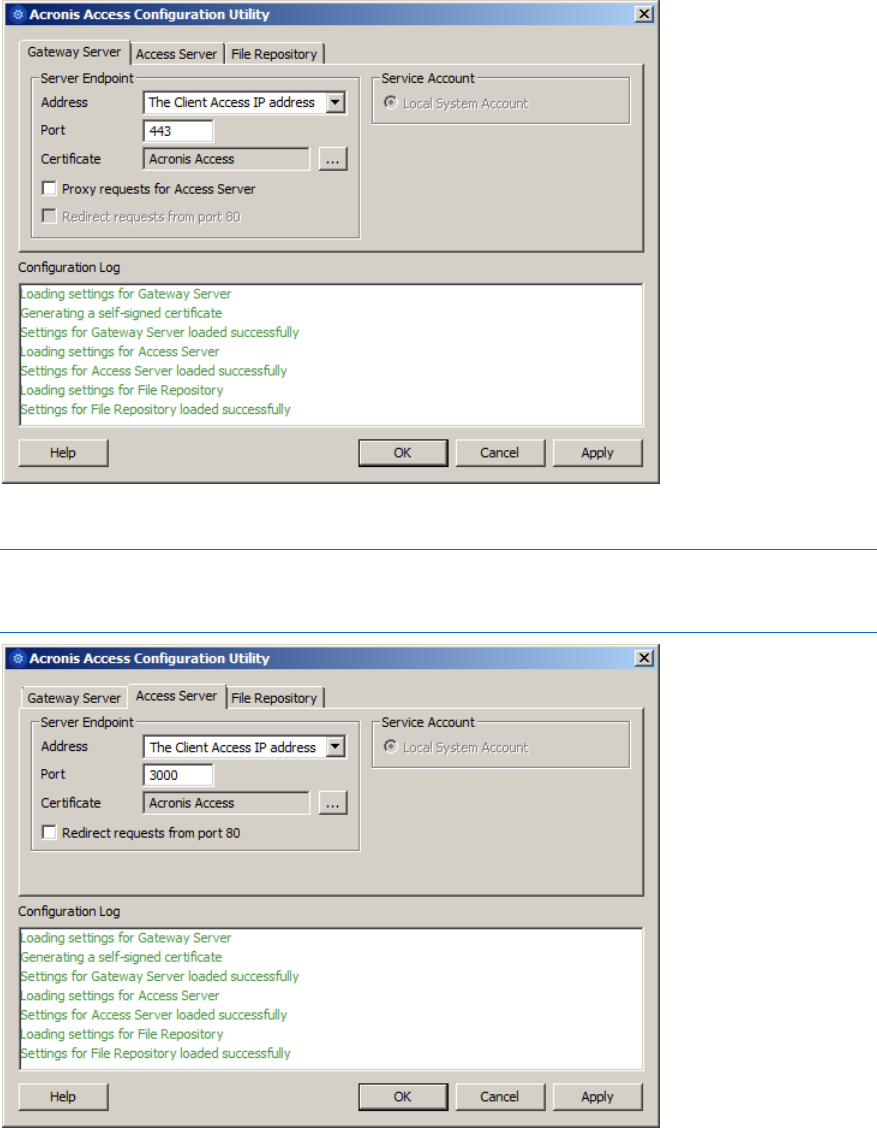
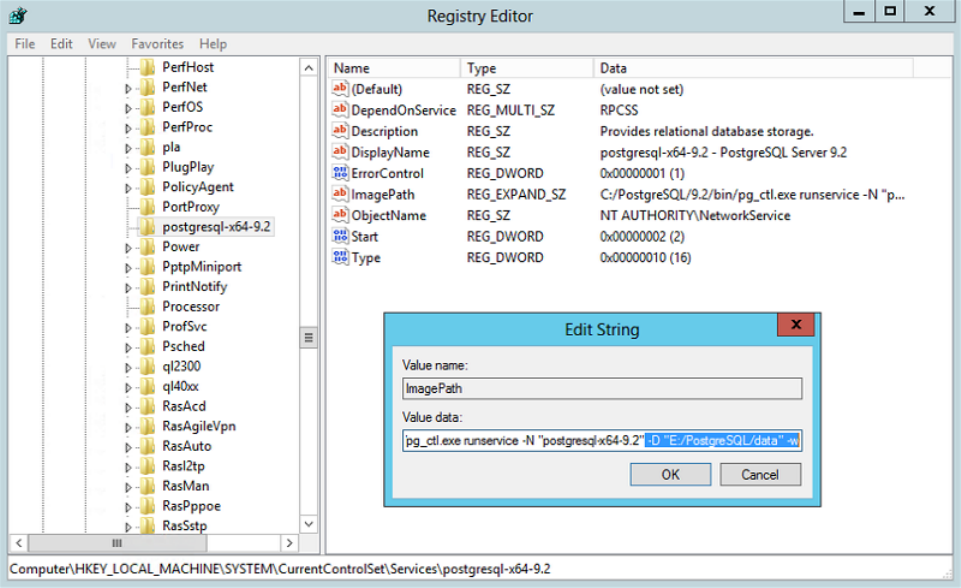
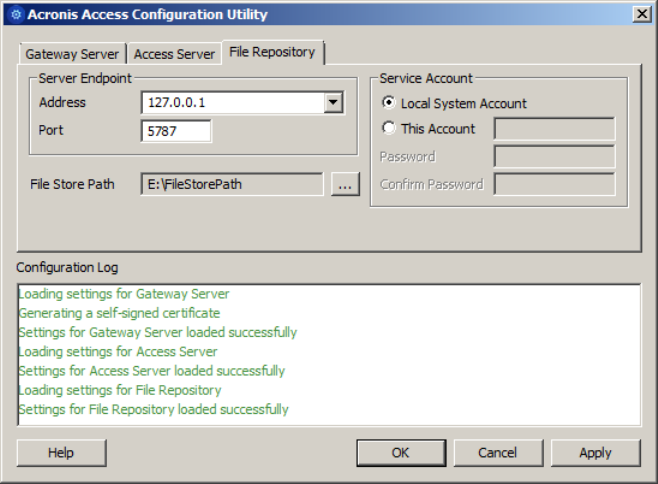
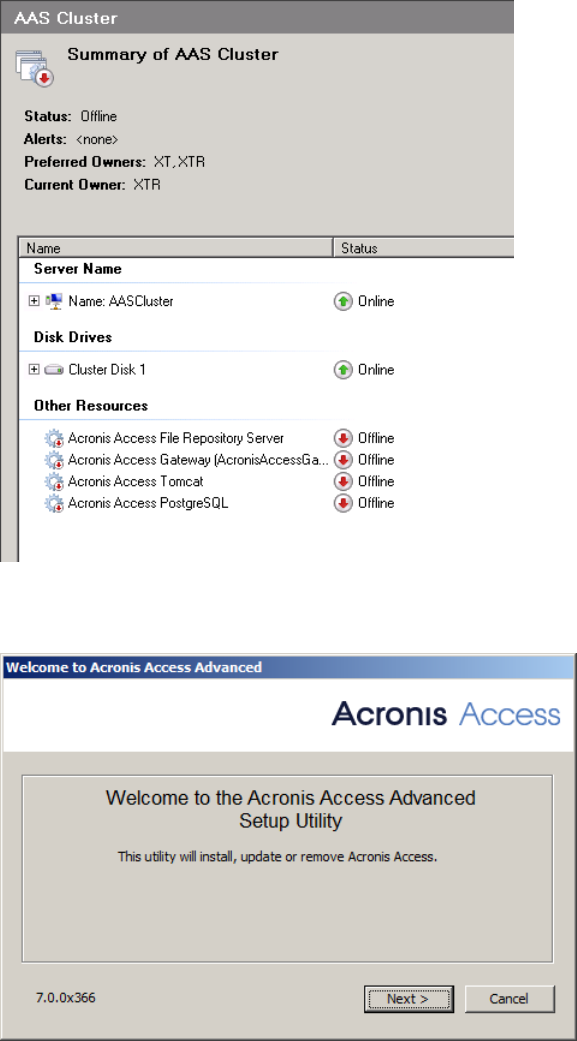
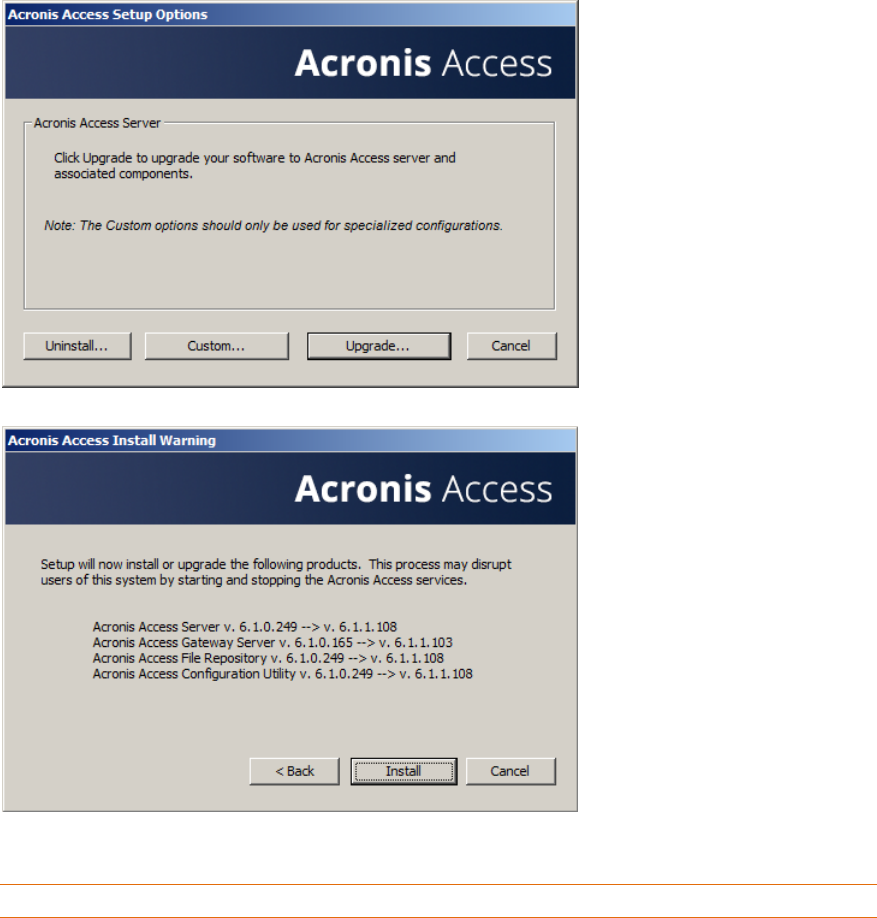
2 Copyright © Acronis International GmbH, 2002-2015
Copyright Statement
Copyright © Acronis International GmbH, 2002-2015. All rights reserved.
“Acronis” and “Acronis Secure Zone” are registered trademarks of Acronis International GmbH.
"Acronis Compute with Confidence", “Acronis Startup Recovery Manager”, “Acronis Active Restore”,
“Acronis Instant Restore” and the Acronis logo are trademarks of Acronis International GmbH.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the
United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit
permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial
purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE
EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such
third-parties are detailed in the license.txt file located in the root installation directory. You can
always find the latest up-to-date list of the third party code and the associated license terms used
with the Software and/or Service at http://kb.acronis.com/content/7696
Acronis patented technologies
Technologies, used in this product, are covered and protected by one or more U.S. Patent Numbers:
7,047,380; 7,275,139; 7,281,104; 7,318,135; 7,353,355; 7,366,859; 7,475,282; 7,603,533; 7,636,824;
7,650,473; 7,721,138; 7,779,221; 7,831,789; 7,886,120; 7,895,403; 7,934,064; 7,937,612; 7,949,635;
7,953,948; 7,979,690; 8,005,797; 8,051,044; 8,069,320; 8,073,815; 8,074,035; 8,145,607; 8,180,984;
8,225,133; 8,261,035; 8,296,264; 8,312,259; 8,347,137; 8,484,427; 8,645,748; 8,732,121 and patent
pending applications.